Protecting our private and secure information is difficult enough at home. Travel amplifies these risks: the devices we carry may be lost, stolen, or seized. Best practices can help in all three cases, but the possibility of seizure, especially at borders, introduces additional personal and legal complications if proper precautions are not taken (1). This report outlines protective strategies that hold up even in extreme scenarios.
Let’s assume you are an honest person operating within the acceptable legal boundaries of your country, business and place of residence. You are about to travel across borders.
Even if you have nothing to hide, personal information can be misinterpreted or deemed unacceptable depending on local laws, political and cultural context. The percentage of people who have their devices confiscated and inspected is small, but the consequences both personally and professionally can be severe.
If your device is seized for interrogation by border agents or law enforcement, special tools might be used to access its contents. You could be compelled to unlock your device or risk detainment, even if you hold high-level credentials or clearances.
Travelers have been detained or denied entry over seemingly minor issues—such as photos or emails—that may not reflect their personal beliefs or behavior. Once your device is unlocked, its contents can be copied, and your ability to object is limited.
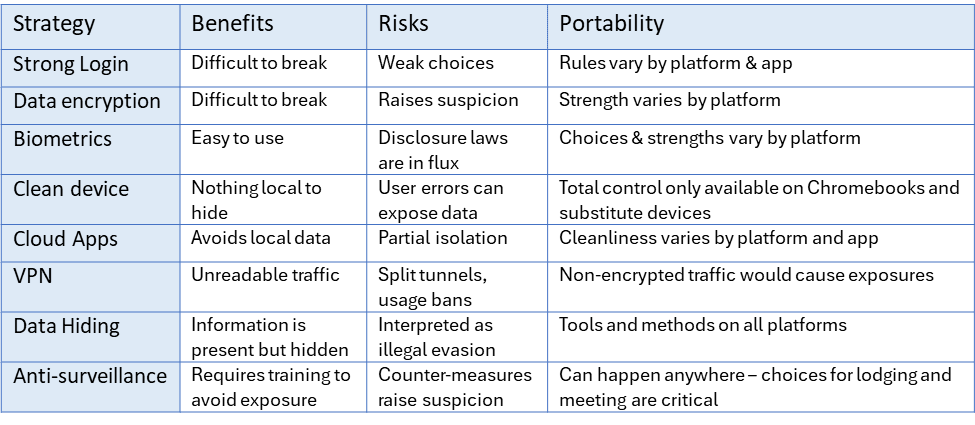
Essential Protections: Keep Your Devices Locked and Encrypted
If you do not have login authentication on your devices, then you are inviting a disaster. You must protect your devices with the strongest available authentication methods and full storage encryption. If you are limited to passwords and PIN codes, make them strong and difficult to guess. Lost or stolen devices will likely be resold for hardware value. Replacing your device is a far smaller price to pay than having your personal information trafficked on the dark web.
Use full-volume on-device data encryption, available on Android, iPhone, Mac OS and Windows devices. Note that older devices may not be encrypted by default and a rewrite process could be required to achieve full protection.
If your device and your apps support multifactor authentication, you have a stronger default defense against loss and theft. However, some of these authentications have their own weaknesses especially if the second factor is communicated through the device being protected. For example a texted access code can be read in real time by another person if your phone’s SIM card has been cloned. In these cases an external or “out of band” factor, such as a token accessory, offers additional strength.
Don’t pin your hopes on single biometric tests, such as facial, iris, or fingerprint recognition. They are convenient, but don’t rely on them alone. Because these traits are always visible, you might be compelled to unlock your device. US Courts are issuing conflicting rulings on this matter, and constitutional protections against searches and seizures can be waived at borders under the Border Search Exception doctrine (2).
In the case of phones and tablets, a full shutdown generally disables most access methods and reverts to your local password or PIN. It’s a good idea to fully shut down all devices before passing through crossings or leaving your device unattended. You cannot be forced to reveal your password or PIN, but as previously mentioned, failure to cooperate could get you detained.
Cleanliness Counts: Travel with a Fresh Device
Your goal is to have no history, social media or old photos, videos or letters to trigger deeper investigations. Remove unnecessary information from your devices before you hit the trail. It’s easy to set up secondary personal and business email accounts and to use these on your travel devices. Log out of unnecessary apps. Be careful to disable cross-device synchronization, password caching, cookies, etc.
Memorize only the essential passwords you’ll need. Leave other sensitive credentials stored securely at home or work, where a trusted contact can access them if necessary.
You may find it easier to set up a secondary device for travel, either your own spare or a loaner device from your company that only has minimal accounts.
Companies looking for ultimately clean loaner solutions may want to consider Chromebooks outfitted with Google’s ChromeOS with Chrome Enterprise Upgrade (3). This enables managed guest sessions and ephemeral profiles, allowing shared devices to operate without retaining user data. When a user signs in, their workspace syncs from the cloud, and when they sign out, the profile is deleted. Administrators control this process, ensuring that users have no direct access to device configurations or stored content—making the system ideal for secure, stateless computing across locations.
Leave Your Data At Home: Do Everything in the Cloud
This solution requires cautious planning. Even with careful privacy setups and use of SSL, many browsers still cache files and cookies locally by default, posing a hidden risk. The first step is to use only web apps that exist on servers that you can trust.
The second step is to access your web apps through browsers that are designed to leave no traces on the user device (4). This might cause compatibility issues with some web apps. And, there still may be recovery tools that can still find some data.
The third step is to transact your browser traffic through a browser or supplemental VPN that will avoid unintended split tunneling (5). SSL alone doesn’t guarantee to prevent the risk of split tunneling where some traffic doesn’t go through the VPN.
Don’t Try to Hide Things: Evasion Is a Crime Everywhere
There is a difference between avoidance and evasion. Anything you do that conceals, masks or distorts information would be considered evasion and can cause serious legal complications. Examples include encrypted and/or hidden partitions, folders and files, and steganography (6). Dual-boot and VMs can also raise suspicion. The technical skill of border agents and police varies, but you should never assume they won’t detect concealed data.
Act Like You Are Being Watched: And Stay On Your Best Behavior
You don’t need to act suspicious to attract attention. Your employment, behavior, patterns, contacts, and internet and phone activities may raise red flags (7).
Assume your communications, locations, and even ambient conversations may be monitored. Your hotel may have cameras and microphones. Don’t engage in sensitive work or personal discussions over unsecured channels while in transit or in uncertain jurisdictions. VPNs might shield your traffic, but they may be banned or raise suspicion in certain countries and jurisdictions. Be cautious about Bluetooth, RFID, AirDrop and open Wi-Fi.
Anything that can happen, will happen.
A Rule For Travelers To Live By
If you wouldn’t say it or send it on a postcard, don’t do it while traveling!
---------------------
References
1. Increasing rates of device inspections andconsequences (US example)
National Law Review
Harvard University
2. Biometric Privacy Challenges (US example).
BorderSearch Exception doctrine
3. Google can achieve total control of Chromebookprofiles and data.
Chrome Enterprise Upgrade
4. Browsers with enhanced Privacy features (no recommendations, not an exhaustive list).
Brave Browser Shields, Opera Secure Private Browser, Waterfox, BitBrowser
Browsers may also offer their own built-in VPNs.
5. Virtual Private Networks (VPNs)
Enterprise networking systems and cloud-based business solutions offer VPNs.
Personal VPNs help with non-business use cases. Examples of 3rd-party reviews:
PC Magazine, PC World,Forbes
6. Example of concealment of information
Steganography
7. Surveillance examples
U.S. Department of State warnings about Chinese Hotels
Tracking of traveler phone locations
---- ---- ---- ---- ---- ----
John Girard
Advisor at Lionfish Tech Advisors, Inc.
_____________________________________
©2025 Lionfish Tech Advisors, Inc. All rights reserved.
Title background image (C) Lionfish Tech Advisors Inc.